- HOME
- Sustainability
- CSR Activity Report (CSR Guideline Activity Reports)
- Risk Management
- Addressing Information Security Risks
Addressing Information Security Risks
Toray Group regards information security as an important management issue and is working to maintain and enhance it across the entire Group. As part of this effort, it established the Toray Group Information Security Basic Policy, which outlines how all executives and employees, including contracted, part-time, and dispatched employees, are expected to fulfill the Group’s social responsibility concerning information security.
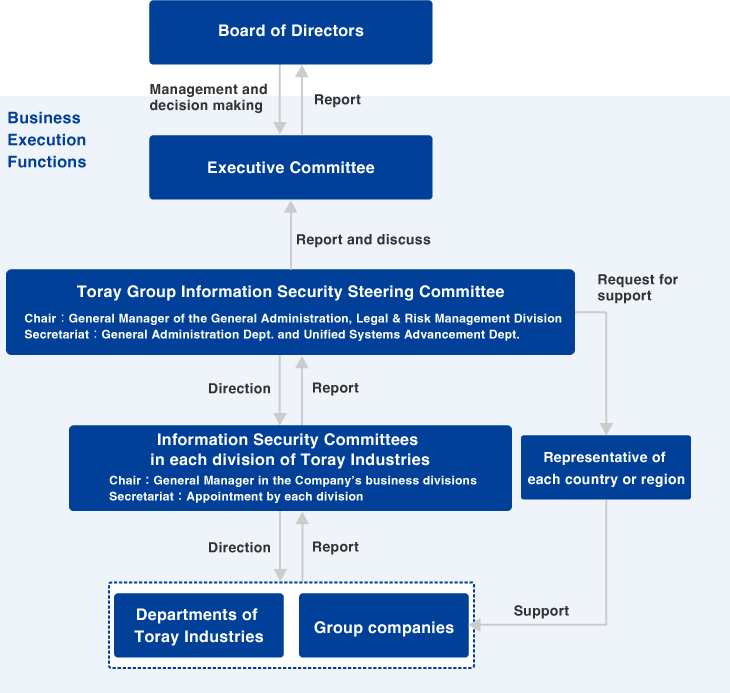
In terms of structure, the Toray Group Information Security Steering Committee has been established to promote information security across the entire Group. Meeting every six months, it is chaired by the general manager of the General Administration, Legal & Risk Management Division at Toray Industries1, with the general manager of the Digital Solutions Division as vice-chair1. The members include representatives from the Human Resources Division, Auditing Department, and other relevant departments.
The committee deliberates on information security policies and discusses risk mitigation measures. It also issues instructions to the Information Security Committees set up in each division, conducts follow-up on progress made, and reports the activities to the Company’s Executive Committee.
The Information Security Committees in each division provide instructions on security measures to their respective departments within Toray Industries, and to the group companies they oversee, and monitor each situation accordingly.
The main activities of the Toray Group Information Security Steering Committee are as follows and are reported to the Board of Directors after being deliberated by the Executive Committee, which acts as a consultative body.
Secretariat:General Administration Dept. and Unified Systems Advancement Dept.
in each division of Toray Industries
Secretariat:Appointment by each division
Toray Industries
each country or region
decision making
support
Execution
Functions
- Ascertaining the risk situation across the entire Toray Group and staying informed on global trends
- Formulating Toray Group information security standards2 and monitoring progress
- Toray Industries has established security standards that comprehensively address risk factors such as cyberattacks, insider misconduct, employee operational errors, and natural disasters. These standards take into account the three elements of information security, namely, confidentiality, integrity, and availability. In addition to technical IT measures, they also include administrative and operational measures such as the management of information assets and education and training aimed at raising employee awareness. These standards also apply to business partners and cloud services used by the Company.
Moreover, after conducting information security audits across Toray Group to check compliance with the standards, Toray Industries identifies areas for improvement and provides guidance as necessary. - Group companies also conduct self-assessments to determine whether they are meeting the standards. They then develop improvement plans, which Toray Industries reviews and provides guidance on.
- Toray Industries has established security standards that comprehensively address risk factors such as cyberattacks, insider misconduct, employee operational errors, and natural disasters. These standards take into account the three elements of information security, namely, confidentiality, integrity, and availability. In addition to technical IT measures, they also include administrative and operational measures such as the management of information assets and education and training aimed at raising employee awareness. These standards also apply to business partners and cloud services used by the Company.
- Conducting regular diagnostic security assessments and monitoring
Having third-party information security companies evaluate Internet security and performance at group companies (and as part of vulnerability analysis, conducting hacker attack simulations, etc.). Also, following up on progress made by group companies. - Ensuring immediate response and prevention of damage escalation in the event of a security incident
Any department or group company discovering an incident must report it within 24 hours to the general manager of the General Administration, Legal & Risk Management Division. Depending on the scale of potential or actual damage, actions must be taken according to predetermined procedures to notify relevant internal and external stakeholders and prevent damage from spreading.
- 1 As of July 2025, a senior vice president serves as general manager of the General Administration, Legal & Risk Management Division and a corporate vice president serves as general manager of the Digital Strategy Division.
- 2 Toray Group information security standards have been developed with reference to information security standards issued by the International Organization for Standardization (ISO) and the National Institute of Standards and Technology (NIST) and using advice from external security companies.
Policies
Toray Group Information Security Basic Policy:Established in April 2022
Toray Group prioritizes information security as an important management issue. In order to fulfill the Group's social responsibility, all officers and employees (including contract, part-time, and dispatched employees) take thorough measures based on the Information Security Basic Policy.
- Ethics and compliance
We will prohibit ourselves from collecting, moving or using any information assets illegally in violation of the regulation or law where Toray group engages their duties. - Development and operation of systems and rules
In order to promote information security measures and to respond promptly to information leaks, we have established an information security system. We will establish a system and rules for security and apply them appropriately. - Protection of information
We will protect the information of our customers and the Toray group companies in accordance with the significance of risk. From the perspective of the protection of personal information, we will protect the personal information of our employees, customers, and Toray group companies from being used for any purpose other than its original intent. - Availability of information assets in support of business continuity
We will secure the availability of information assets necessary to pursue and fulfill our social responsibility. - Continuous Improvement and Maintenance of Information Security
We will continuously improve the information security management system by prioritizing identified issues, by continuously conducting risk analysis of emerging threats, changes to the business, and or the evolution of information technology.
Combating Cyber Attacks
Toray Group is taking a range of measures to combat today’s increasingly sophisticated cyberattacks. In addition to efforts aimed at preventing such incidents, the Group has implemented measures to mitigate risks in the event of a damaging attack.
- Compliance with Toray Group information security standards
Each group company establishes its own information security management system. After identifying information assets such as computer terminals, servers, user IDs, confidential information, and personal data, the companies define and implement rules for managing and securing each asset. They also regularly check their security management situations.
Security measures also include procedures for responding to security incidents, securing backups for system recovery, and preparing recovery procedures. - Device management
Toray Industries has standardized settings for its computers and smartphones and has established an Endpoint Detection and Response (EDR) system for centralized management of these devices, and for enabling quick detection of and response to any cyberattacks. These measures are being expanded across the Toray Group. - Authentication management
Toray Industries has established a system for centralized management of user IDs and utilizes multi-factor authentication (MFA). This initiative is also being expanded across the Group. - Network management
- (1) Toray Industries and its group companies constantly monitor communications between the Internet and their own internal networks.
- (2) Toray Group conducts regular risk assessments of Internet security and performance using third-party security companies and implements all necessary improvements.
- Server and cloud service management
Toray Group maintains server and cloud service ledgers. Toray Industries has also developed a group-wide shared server environment with security monitoring capabilities, which is being adopted across the entire Group. - Strengthening Monitoring and Response Systems
Information from monitoring and analysis related to endpoint, authentication, network, and server management has been consolidated to detect cyberattacks and enable a prompt response. In the event of a security incident, information is shared with executive management and relevant risk management departments to ensure measures are taken to minimize potential damage. - Enhancing education and training
As IT measures alone may not be sufficient to address today’s increasingly sophisticated cyberattacks, the Group also conducts education through regular e-learning for all employees (once a year) and training sessions on responding to unsolicited email.
Prevent Employees from Leaking Confidential Information
Toray Group implements a range of measures in accordance with the Toray Group information security standards.
In addition to providing information security education for all employees on an annual basis, Toray Group conducts level-specific training for employees, including new employees and newly appointed managers. The aim is to improve security awareness and skills, while also thoroughly disseminating the Toray Group Information Security Basic Policy.
At the same time, an e-mail magazine is sent out regularly and a series on information security is carried in an in-house magazine to encourage the improvement of information security literacy among all employees.
Before removing a computer or smartphone from an office, for example, employees must receive permission from a manager. In addition, the actual device must be inspected monthly, and an inventory of assets is taken once every six months.
Moreover, the Group has established approaches to dealing with the loss of such devices and other similar incidents, and has built channels for reporting and other mechanisms to minimize damage thereof.
Click here for the main initiatives for CSR Guideline 5, "Risk Management" in CSR Roadmap 2025.